Blockchain technology has revolutionized the way we handle digital transactions and data, offering a transparent, secure, and decentralized approach to managing information. Central to the success of blockchain is its security measures, and one of the most fundamental aspects of this security is hashing.
In this article, we will delve into the critical role of hashing in enhancing the security of blockchain technology. Hashing is a process that plays a pivotal role in ensuring the integrity and authenticity of data on the blockchain, making it a cornerstone of blockchain security.
Understanding the importance of hashing in blockchain is essential for anyone interested in the world of technology, finance, and data security. We will explore the concept of hashing, its role in securing data on the blockchain, and its implications for the future of digital transactions. By the end of this article, you will have a comprehensive understanding of how this cryptographic technique bolsters the trustworthiness and immutability of the blockchain.
So, let's embark on a journey into the world of blockchain security, starting with a fundamental concept: how hashing helps secure this revolutionary technology.
Table of Contents
Understanding Blockchain Technology
Before we dive into the significance of hashing in securing blockchain technology, it's crucial to have a solid grasp of what blockchain technology is and how it functions.
At its core, a blockchain is a distributed ledger that records transactions across a network of computers. What sets it apart from traditional centralized databases is its decentralized and immutable nature. Instead of relying on a single central authority to maintain and validate the ledger, blockchain leverages a network of nodes, each participating in the verification process.
Here are some key elements of blockchain technology to understand:
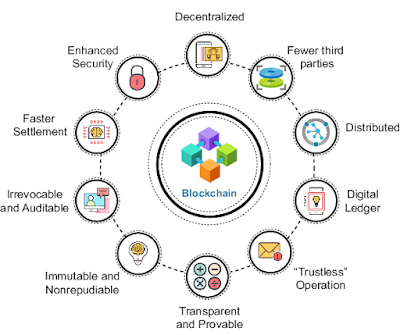
Decentralization: Blockchain operates on a decentralized network of nodes. Each node has a copy of the entire ledger, ensuring no single point of control. This decentralization enhances security by eliminating the vulnerability of a central authority.
- Transparency: All transactions on the blockchain are visible to every participant. This transparency not only builds trust but also allows for public verification of transactions.
- Immutability: Once a transaction is recorded on the blockchain, it cannot be altered or deleted. This immutability is crucial for maintaining the integrity of the ledger.
- Consensus Mechanisms: Blockchains use consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS) to validate and add new transactions to the ledger. These mechanisms ensure that all nodes agree on the state of the blockchain.
- Smart Contracts: Many blockchains support smart contracts, self-executing contracts with the terms of the agreement directly written into code. These contracts automate and enforce the execution of agreements.
Understanding these core principles of blockchain technology is essential as it forms the basis for comprehending how hashing contributes to the security of this revolutionary technology.
Now that we have a foundational understanding of blockchain, let's explore how the process of hashing plays a vital role in maintaining the trust and security of this decentralized ledger.
The Role of Hashing in Blockchain Security
Hashing is a fundamental concept in the world of cryptography and plays a pivotal role in securing blockchain technology. But what exactly is hashing, and why is it so crucial in the context of blockchain security?
Hashing Defined:
In simple terms, hashing is the process of taking an input (or 'message') and transforming it into a fixed-size string of characters, which is typically a sequence of numbers and letters. This output is known as the hash value or hash code. The key characteristic of a cryptographic hash function is that it's a one-way function, meaning it's nearly impossible to reverse the process and determine the original input from the hash value.
Now, let's explore the primary functions of hashing in blockchain security:
1. Data Integrity:
One of the fundamental uses of hashing in blockchain is to ensure the integrity of data. When a transaction is recorded on the blockchain, it's hashed. Any subsequent alteration of the transaction would result in a different hash value. This makes it exceptionally difficult for anyone to tamper with the data, as it would require changing not only the transaction but also all subsequent blocks in the chain. This property safeguards the data from unauthorized modifications, enhancing trust in the system.
2. Efficiency and Speed:
Hashing allows for quick and efficient data verification. Instead of comparing entire blocks of data, nodes can compare hash values to check the integrity of information. This speeds up the verification process and reduces computational overhead, making blockchain more efficient.
3. Public Verification:
The hash values of transactions are publicly available and can be used for verification by anyone on the network. This transparency allows users to independently confirm the accuracy of transactions and maintain trust in the system without relying on centralized authorities.
4. Cryptographic Security:
Cryptographic hash functions are designed to be secure against various attacks. They have specific properties like collision resistance, meaning it's extremely difficult to find two different inputs that produce the same hash. This security ensures the reliability of the blockchain.
Understanding these roles of hashing in blockchain security is vital, as it forms the basis for the trust and immutability that blockchain technology offers. Hashing is a crucial tool that protects the integrity and authenticity of data on the blockchain, making it a foundational element of blockchain's success.
Cryptographic Hash Functions
To fully comprehend the role of hashing in securing blockchain technology, it's essential to explore cryptographic hash functions in detail. These functions are the building blocks of data integrity and security in the blockchain world.
Properties of Cryptographic Hash Functions:
- Deterministic: A cryptographic hash function always produces the same hash value for a given input. This determinism ensures consistency and predictability.
- Fast Computation: Hash functions are designed for efficient computation. They generate hash values quickly, making them suitable for real-time transaction verification in blockchain networks.
- Fixed Output Size: Regardless of the input size, cryptographic hash functions produce a fixed-size output. This fixed length is a crucial characteristic for maintaining the integrity of blockchain data.
- Pre-image Resistance: Given a hash value, it should be computationally infeasible to determine the original input. This property makes it challenging for malicious actors to reverse engineer the data.
- Collision Resistance: It should be extremely unlikely for two different inputs to produce the same hash value. Collision resistance is vital in preventing unauthorized alterations to blockchain data.
- Avalanche Effect: A small change in the input should result in a significantly different hash value. This property ensures that even a minor alteration to the data produces a vastly different hash, making tampering virtually impossible.
Non-reversible: Hash functions are one-way functions, meaning you can't reverse the process to determine the original input from the hash value. This adds a layer of security to the data.
Common Cryptographic Hash Functions:
In the world of blockchain and cryptography, several widely used cryptographic hash functions include:
- SHA-256 (Secure Hash Algorithm 256-bit): This hash function is notably used in Bitcoin and many other cryptocurrencies. It's highly secure and has a fixed output size of 256 bits.
- SHA-3: The third generation of the Secure Hash Algorithm family, SHA-3 is designed to provide security against future attacks and vulnerabilities.
- MD5 (Message Digest Algorithm 5): Although widely used in the past, MD5 is now considered outdated and vulnerable to collisions. It's no longer suitable for secure applications.
Understanding these properties and the importance of cryptographic hash functions is vital for grasping how blockchain technology achieves its security and immutability. In the next section, we will explore in depth how hashes are employed to secure data on the blockchain, ensuring its trustworthiness and authenticity.
How Hashes Secure Data on the Blockchain
Now that we've established the importance of cryptographic hash functions, let's explore how these hashes are employed to secure the data on the blockchain, ensuring its trustworthiness and authenticity.
Transaction Verification:
In a blockchain network, each transaction is hashed before it is added to a block. This initial hash serves as a unique identifier for the transaction. When multiple transactions are added to a block, their hashes are also included in the block's header.
- Merkle Trees: To ensure efficient verification and quick access to specific transactions, a Merkle tree structure is used. This tree organizes the transaction hashes in a hierarchical way, allowing nodes to verify individual transactions without needing to traverse the entire block.
- Linking Blocks: Each block on the blockchain contains not only a list of transactions but also the hash of the previous block. This linking of blocks via their hashes creates a chain, and any attempt to tamper with a block would require recalculating the hash for that block and all subsequent blocks. This makes the blockchain highly secure against data manipulation.
- Consensus Mechanisms: Blockchain networks rely on consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS) to validate and add new blocks to the chain. These mechanisms ensure that all nodes on the network agree on the state of the blockchain. Hashes play a crucial role in reaching consensus, as nodes use hash values to validate the integrity of transactions.
- Public Verification: The transparency of the blockchain allows anyone to verify the integrity of transactions by checking the hash values. If a single bit of data within a block is altered, the hash value changes, alerting the network to a potential issue. This public verification process builds trust and ensures that the blockchain remains tamper-proof.
- Smart Contracts: Smart contracts, a feature of some blockchains, also rely on hashing to ensure their security. The contract terms and conditions are hashed, and the contract's execution depends on these hashed conditions. Any modification to the contract terms would result in a different hash value, preventing unauthorized changes.
- Cryptographic Security: The collision resistance and pre-image resistance properties of cryptographic hash functions make it extremely difficult for malicious actors to alter data on the blockchain without detection. This cryptographic security is a cornerstone of blockchain technology.
In essence, cryptographic hash functions and their use in hashing transactions and blocks make the blockchain a secure and trustworthy ledger. The decentralized and transparent nature of blockchain, combined with the cryptographic security of hashing, creates a system that's incredibly resistant to tampering and fraud.
Protecting Against Tampering
One of the paramount objectives of blockchain technology is to protect data from tampering and unauthorized alterations. Hashing, as we've discussed, plays a pivotal role in achieving this goal, and it does so through a combination of cryptographic principles and blockchain's unique structure.
Here's how blockchain, with its robust use of hashing, safeguards against tampering:
1. Immutability Through Hash Chaining:
Every block on the blockchain contains a reference to the previous block's hash. This chain of hashes links each block to its predecessor, creating a sequential structure. To alter the data in a block, an attacker would not only need to change the content of that block but also recalculate the hash for that block and all subsequent blocks. This is an extremely challenging task, as it would require an immense amount of computational power and would be easily detected by the network.
2. Transparency and Public Verification:
Every transaction and block on the blockchain is publicly available for verification. The hash values serve as unique fingerprints for each piece of data. If even a single bit of data is tampered with, the hash value changes and this alteration becomes visible to everyone on the network. The transparency of blockchain enables anyone to independently verify the integrity of the data without relying on centralized authorities.
3. Cryptographic Security:
Cryptographic hash functions used in blockchain, like SHA-256, are designed to be secure against various attacks. They exhibit properties such as collision resistance, making it exceptionally difficult for two different inputs to produce the same hash. This cryptographic security prevents attackers from exploiting vulnerabilities in the hashing process.
4. Consensus Mechanisms:
Blockchain networks rely on consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS) to validate and add new blocks to the chain. Nodes in the network use hash values to verify the integrity of transactions and blocks. Consensus mechanisms ensure that all participants agree on the state of the blockchain, making it even more resistant to tampering.
5. Smart Contracts:
Smart contracts, which are self-executing agreements on some blockchains, also rely on hashing to ensure their security. The contract terms and conditions are hashed, and the execution of the contract depends on these hashed conditions. Any unauthorized changes to the contract terms would result in a different hash value, triggering a breach of the contract's conditions.
The robust protection against tampering provided by hashing and the blockchain's structure is a critical factor in the trustworthiness of blockchain technology. Users can have confidence that once data is recorded on the blockchain, it is secure and immutable, making it a reliable platform for a wide range of applications beyond just cryptocurrencies.
Examples and Use Cases
The secure and tamper-resistant nature of blockchain technology, empowered by hashing, has found applications in a multitude of industries. Let's explore real-world examples and use cases that illustrate how hashing and blockchain security are harnessed in various scenarios:
1. Cryptocurrencies: The most well-known application of blockchain technology is cryptocurrencies like Bitcoin. Blockchain's use of hashing ensures that each transaction is immutable, transparent, and resistant to tampering. The SHA-256 algorithm plays a crucial role in securing the Bitcoin blockchain.
2. Supply Chain Management: Blockchain is used to track the origins and movements of products within supply chains. Each step in the supply chain can be recorded as a transaction, and the transparency and immutability of blockchain, backed by hashing, ensure that the information is trustworthy and can't be altered.
3. Healthcare: Patient records, drug traceability, and clinical trial data can be securely stored on a blockchain. Hashing protects the privacy and integrity of patient information while allowing for efficient access and verification by authorized parties.
4. Voting Systems: Blockchain-based voting systems use hashing to safeguard the integrity of votes. Each vote is hashed and recorded on the blockchain, ensuring that votes are secure, transparent, and tamper-proof.
5. Intellectual Property: Artists, writers, and creators use blockchain to protect their intellectual property rights. Hashing secures digital content, proving ownership and preventing unauthorized reproduction.
6. Real Estate: Property transactions can be recorded on a blockchain, reducing fraud and ensuring the integrity of land registries. Hashing plays a crucial role in securing these records.
7. Cross-Border Payments: International money transfers benefit from blockchain's speed and cost-effectiveness. Hashing ensures the security of transactions, making cross-border payments more reliable.
8. Food Safety: The food industry uses blockchain to trace the origin of products, reducing the risk of contamination and fraud. Hashing verifies the authenticity of product data throughout the supply chain.
9. Notary Services: Blockchain technology can be used as a digital notary, ensuring the authenticity and integrity of legal documents through cryptographic hashing.
10. Gaming and Collectibles: Blockchain is used to verify the authenticity of in-game items, collectibles, and digital assets. Hashing protects the rarity and ownership of these items.
These examples highlight the diverse applications of blockchain technology in various sectors. The common thread in all these use cases is the use of cryptographic hash functions to ensure data integrity, transparency, and security.
As blockchain technology continues to evolve, new use cases and applications are constantly emerging, demonstrating the versatility and potential of this groundbreaking technology.
Challenges and Future Developments
While blockchain technology has made significant strides in enhancing data security through hashing and other cryptographic techniques, it is not without its challenges. Understanding these challenges and the potential future developments is crucial for staying at the forefront of blockchain security.
Challenges:
- Scalability: One of the primary challenges in blockchain technology is scalability. As more transactions are added to the network, the blockchain's size grows, potentially slowing down the verification process. Solving scalability issues while maintaining security is a critical task.
- Energy Consumption: Proof of Work (PoW) consensus mechanisms, while secure, are energy-intensive. This poses environmental concerns and has led to the exploration of more eco-friendly alternatives.
- Interoperability: Different blockchain networks often operate in isolation. Establishing interoperability standards to enable seamless data sharing between blockchains remains a challenge.
- Regulatory Uncertainty: Regulatory frameworks for blockchain and cryptocurrencies are still evolving. The legal and compliance landscape can impact the adoption of blockchain technology.
- Quantum Computing Threats: The advent of powerful quantum computers poses a potential threat to existing cryptographic algorithms, including those used in blockchain. Preparing for this emerging challenge is essential.
Future Developments:
- Scalability Solutions: Innovations like sharding and layer-2 solutions aim to improve blockchain scalability without compromising security. These developments will make blockchain networks more efficient.
- Energy-Efficient Consensus: Transitioning from energy-intensive PoW to more sustainable consensus mechanisms like Proof of Stake (PoS) or Proof of Authority (PoA) will reduce the environmental impact of blockchain networks.
- Cross-Chain Integration: The development of cross-chain protocols and interoperability standards will enable different blockchains to communicate and share data seamlessly, expanding the potential applications of blockchain.
- Regulatory Clarity: As regulatory frameworks mature, the blockchain industry will gain more certainty and legitimacy. Clearer regulations can provide a framework for responsible and secure blockchain development.
- Post-Quantum Cryptography: Research into post-quantum cryptographic algorithms aims to secure blockchain against future threats from quantum computing. These cryptographic advancements will play a critical role in blockchain security.
- Enhanced Privacy: Privacy-focused blockchain solutions are under development to provide users with more control over their data while ensuring security. These solutions will have a significant impact on industries like healthcare and finance.
As blockchain technology continues to evolve, it is expected to become more efficient, environmentally friendly, and secure. Overcoming current challenges and embracing future developments will further enhance the role of blockchain and hashing in securing data in an increasingly digital world.
In this journey through the world of blockchain technology and its reliance on hashing, we've unveiled the bedrock of data security, transparency, and immutability. Blockchain's innovative approach to securing data through cryptographic hash functions has ushered in a new era of trust and efficiency in a wide range of industries.
We've explored the essential properties of cryptographic hash functions: their deterministic nature, efficiency, fixed output size, pre-image resistance, collision resistance, avalanche effect, and non-reversibility. These properties, combined with the unique structure of the blockchain, make data on the blockchain virtually immune to tampering and fraud.
Blockchain's transparency and public verification capabilities, powered by hashing, have transformed industries such as supply chain management, healthcare, voting systems, and intellectual property protection. The trust and authenticity provided by blockchain technology have made it a reliable platform for use cases as diverse as cross-border payments, food safety, notary services, gaming, and more.
Despite the current challenges in blockchain technology, including scalability, energy consumption, and regulatory uncertainty, the future holds promising developments. Scalability solutions, energy-efficient consensus mechanisms, cross-chain integration, regulatory clarity, and advancements in post-quantum cryptography are paving the way for a more efficient, secure, and sustainable blockchain landscape.
As blockchain technology continues to evolve, it is clear that its impact on various sectors and daily life will only grow. The principles of hashing, data integrity, and cryptographic security will remain at the core of blockchain's success, promising a future where trust, transparency, and security in the digital world are more accessible than ever before.
Blockchain and hashing have not only reshaped the way we think about data security but have also ignited a revolution that is driving innovation, efficiency, and trust in the global economy.
In this ever-changing landscape, staying informed about the latest developments and advancements in blockchain technology and hashing will be essential for those seeking to harness the full potential of this transformative technology.
Related Articles:
- The Future of Blockchain Technology | Unlocking its Potential
- The Future of Machine Learning - Trends and Transformations
- Exploring the VR World - A Journey into Virtual Reality Technology
- Quantum Computing for Everyone - Demystified
- Demystifying Datafication | Transforming the World into Information







0 Comments